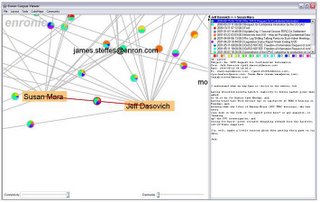
Software takes the emails and generates a map of relationships. It can tell investigators who has been emailing X, and who X emails. The relationships are expressed in the form of a series of diagrams.
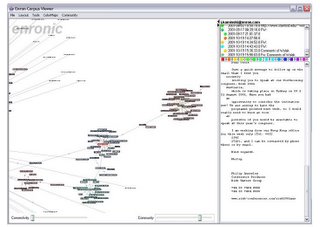
This is a form of traffic analysis and has been used by police and intelligence services for years. The diagrams that are produced are called spider webs. This is a very good name because they are highly effective at trapping people.
Once investigators have one suspect they can analyse their phone calls or emails to identify all their contacts. Find one member of a group of political activists and soon you have them all. Of course, it does not work on professional terrorists or spies. They are well aware of the risks, and know how to stop a web being spun.
Spider webbing is why the EU has passed a data retention directive that will result in all EU internet and telephone traffic being retained and available for analysis. It is also why the FBI is trying to get data retention established in the USA. It’s a great technique for identifying those troublemakers who might disagree with the authorities.
Data retention does not save the content of messages, but it does not have to. Traffic analysis is a very effective technique and does not need to know what was said or written to work.
Spderwebbing also has applications in business as this Wired article explains.
"memos, presentations and other scraps of corporate intelligence are increasingly finding their way into vast "electronic discovery" centers like the one Kroll Ontrack operates here near Minneapolis.
Day and night, rows of whirring, blinking computers sock away enormous batches of digital records sent by companies involved in lawsuits. Other files are discovered deep in hard drives -- wedged between everything from personal e-mails to pornography -- by Kroll Ontrack forensic teams whose code names keep their missions secret."
1 comment:
This horrifies me.
Mr. H.K.
Postcards from Hell's
Kitchen
And I Quote Blog
Post a Comment